Most organizations using SSO for Testersuite do so through Microsoft Entra ID (formerly known as Azure Active Directory or Azure AD). On this page, you will find the specific steps required to set up SSO for Testersuite via Microsoft Entra ID.
1: Create enterprise application in MS Entra
- Go to https://entra.microsoft.com/ and log in with your Microsoft account
- On the left, click "Enterprise apps" and click "New application.

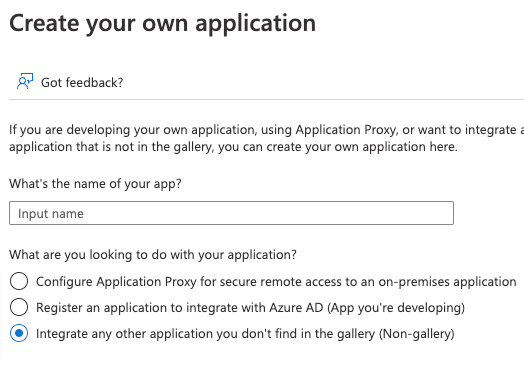
- Then choose "Create your own application" if you do not have these rights, you will need an Entra administrator within your organization to obtain these rights.
- For example, name the application "Testersuite" and below that, choose the "Non-gallery" option from the list:
- Save the settings and within your Enterprise app go to "Single sign-on," choose SAML here:

2: Create SSO configuration in Testersuite
- In another tab, go to the Testersuite administrator portal, choose settings -> SAML SSO and create a new configuration:

- Complete the fields in the form under the Service provider heading:
- Enabled: Check this field to enable your connection. This will display an SSO link on your users' Testersuite login screen.
- Name: Give the SSO configuration a name. This name will be the text for SSO link on the login screen.
- Sp certificate and Sp key: Use a tool such as Samltool.com to create a new X.509 certificate. The State/Province Name, Organization Name and Common Name fields are required. Exactly what you enter here is not important, but these fields are required to generate the certificate. Set a distant expiration date to prevent maintenance. Do not set a passphrase for the private key. Fill in the Sp certificate and Sp key fields with the information obtained.
- Complete the fields in the form under the Identity provider heading:
- Fill the Testersuite field Idp Entity id with the value found in your Enterprise app in Entra in the 'Microsoft Entra Identifier' field. Fill the Testersuite field Single sign on service location with the value found in your Enterprise app in Entra in the 'Login URL' field:

- Idp username attribute: For now, fill this field with a fictitious value, for example 'Username'. We will get the real value later from Entra.
- Idp certificate: Fill this field for now with the value from the Testersuite field Sp certificate. We will replace this later with the correct value from Entra.
- Idp sign metadata: Some identity providers require the metadata to be signed. Check this option if this is the case.
- Save the configuration in Testersuite .
3: Enter Testersuite values into Entra
- Open the configuration in Testersuite and copy the URL in the Service provider -> Entity ID field. Enter this in Entra, in theIdentifier (Entity ID)field:

- In Testersuite , click on the link in the 'Metadata' field and copy the value in the XML field 'AssertionConsumerService -> Location'. Enter this value in Entra, in the 'Reply URL (Assertion Consumer Service URL)' field:

4. Enter Entra values in Testersuite
- In the Enterprise app in Entra, click Edit in the Attributes & Claims block:

- Choose the claim that matches the username in Testersuite, and for the appropriate claim, copy the value in the 'Claim name' field, for example, for the claim 'Emailaddress' when the Testersuite usernames match the email addresses of the users in Entra:

- Enter this value in Testersuite , in the 'Idp username attribute' field:

- In Entra, download the Base64 encoded certificate from the SAML certificates block:

- Enter this certificate in Testersuite , in the 'Idp certificate' field:

- After setting these fields, save the configuration in Testersuite. Users can then log in using the SSO link you created on the Testersuite login screen.
Note that only users who have been granted access to the Testersuite Enterprise application in Entra can use SSO.